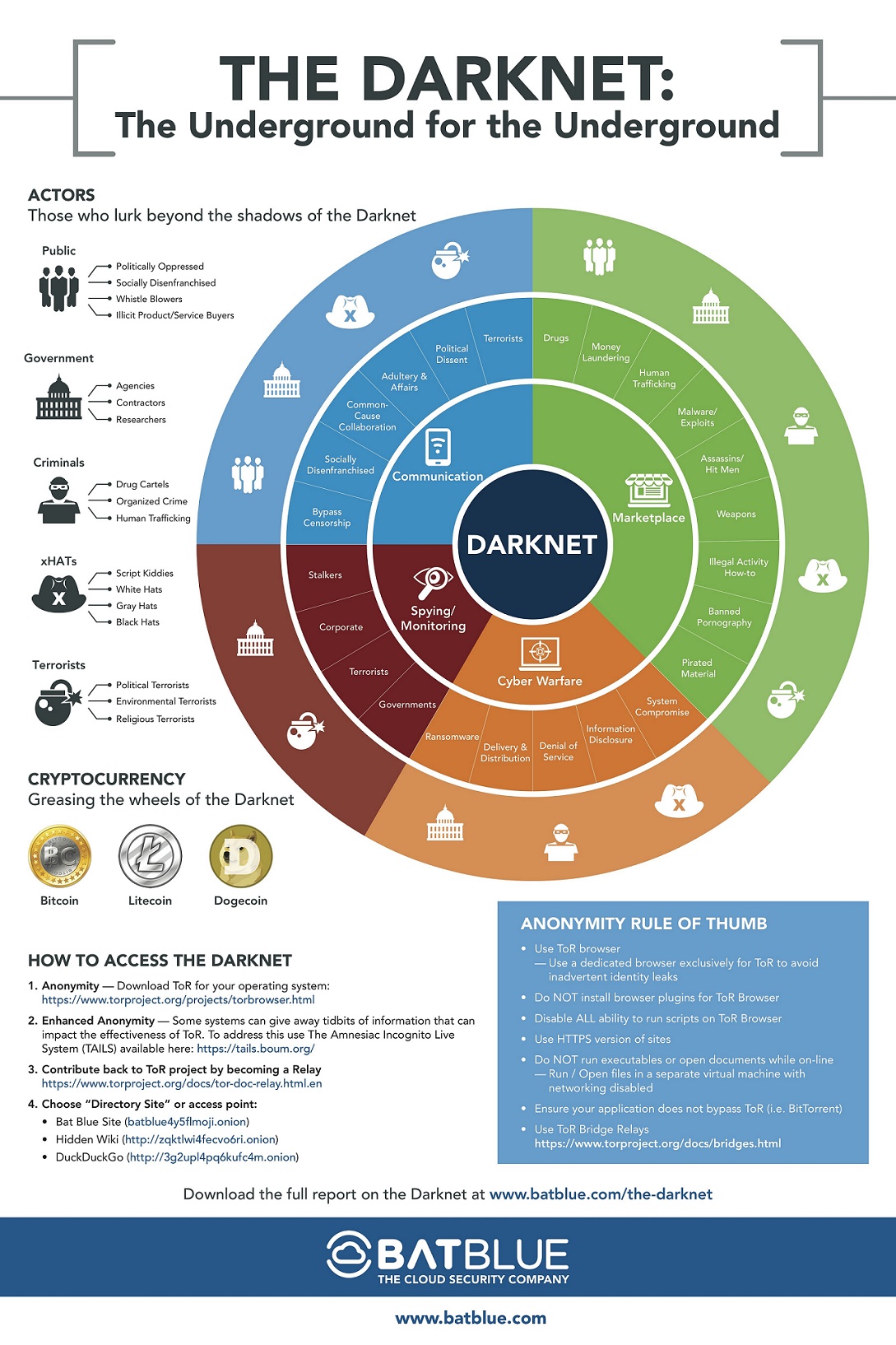
Malaysia dark net
In order to avoid occurrence bad thing happen in the future, we have to get enough information and knowledge of the thing that want to avoid First I would like to share some documentary movies about darkweb and secound i write about darknet in Malaysia .
Documentary/TV
series 2013
Cyber Secrets is an educational web series that covers subjects ranging from digital forensics to hacking computers to security and intelligence gathering. Since the series covers so many subjects, everyone can learn something from watching. The first episodes cover Anonymity and the Tor Onion routing network. After that, the coverage moves toward forensics and then to hacking / system exploitation
Written by Jeremy Martin
2. Dark Net
Creator / Mati Kochavi
--
A documentary series that explores the furthest reaches of the internet and the people who frequent it, Dark Net provides a revealing and cautionary look inside a vast cyber netherworld rarely witnessed by most of us.
A documentary series that explores the furthest reaches of the internet and the people who frequent it, Dark Net provides a revealing and cautionary look inside a vast cyber netherworld rarely witnessed by most of us.
3. Dark Web
When Elizabeth Wallace's husband is arrested for running an Internet sub-network her charmed life is turned upside down when she is expected to carry on in the family business where he left off
Director and Writer: Alex winter
A feature documentary that explores the rise of a new
Internet; decentralized, encrypted, dangerous and beyond the law
· Brooklyn Film Festival 2015 Nominated /Festival award Best documentary feature / alex winter
· Montclair Film Festival (MFF) 201 Nominated/ Bruce Sinofsky Prize for Documentary Feature
· Zurich Film Festival 2015 Nominated/ Golden Eye
· Montclair Film Festival (MFF) 201 Nominated/ Bruce Sinofsky Prize for Documentary Feature
· Zurich Film Festival 2015 Nominated/ Golden Eye
Movie Awards
Best International Documentary Film/ Alex Winter
Tacklin This video about a global coalition of cyber-police pulled off one of the biggest sting operations in their history. It’s being called Operation ON-imm-uhs.
The opposite of ANONYMOUS a bunch of their internet administrators and web retailers are in jail after police in 17 countries all coordinated a big sting operation.
Authorities seized drugs, weapons, computers and illegal items during their coordinated raids. According to government officials in the US, United Kingdom, Ireland, the Netherlands and others, these suspects are now in custody for carrying out illegal acts, all on the Dark Webg Dark Web of crime Friday, 24 June By/ DATUK AKHBAR SATAR Institute of Crime and Criminology Help University Combating criminal activities operating in the Dark Web requires more proactive efforts compared to traditional security. It demands cyber security experts and technical resources combined with an innovative approach.
The Malaysian government has to introduce a dedicated cybercrime unit to tackle the Dark Web. For short-term measures, the relevant law enforcement agencies and regulators should form a task force with Cybersecurity Malaysia and acquire the capabilities pertaining to Deep Web analysis. This is to enable the task force to effectively conduct investigations on serious criminal activities operating in the Dark Web.
For long-term planning, the Government may consider forming a federal crime agency with a range of specialist capabilities to fight serious organised crime. The agency can respond to a wide range of threats including cybercrime, drug, human and weapons trafficking and economic crime. In 2013, the UK government formed the National Crime Agency (NCA) to fight serious and organised crime.
This law enforcement intelligence-led agency has launched a dedicated cybercrime unit to tackle the dark Web. Finally, Malaysia should also introduce a national plan to fight cybercrime. According to the 2014 Global Economic Crime Survey by PricewaterhouseCoopers (PWC), cybercrime will likely emerge as “the most popular” type of economic crime in Malaysia as more IT-related transactions are made in the future.
Prevention and mitigation are other vital aspects in fighting cybercriminals and terrorists especially in the Dark Web. My personal opinion Before I write my opinion I would like to say that Most Malaysians learnt about The Dark Web following the recent of a heinous crime committed by a British pedophile.
It emerged during the trial in which pictures and illicit videos were found posted on The Dark Web.my advice to every one is you must do security tips to help the Internet users minimize the risk of personal data: Update Web Browser, Change Passwords Regularly, Data Encryption.
Be Wary of Public Wi-Fi Filter what you share on Social Networking sites In my opinion, The Malaysia Police must cooperate with Cybersecurity Malaysia to track down organized criminal activities such as pedophiles in the country as the Director of the Institute of Crime and Criminology, University HELP, Datuk Akhbar Satar said above .
Source : http://www.thestar.com.my/opinion/letters/2016/06/24/tackling-dark-web-of-crime/
https://www.youtube.com
https://www. imdb.com/
The opposite of ANONYMOUS a bunch of their internet administrators and web retailers are in jail after police in 17 countries all coordinated a big sting operation.
Authorities seized drugs, weapons, computers and illegal items during their coordinated raids. According to government officials in the US, United Kingdom, Ireland, the Netherlands and others, these suspects are now in custody for carrying out illegal acts, all on the Dark Webg Dark Web of crime Friday, 24 June By/ DATUK AKHBAR SATAR Institute of Crime and Criminology Help University Combating criminal activities operating in the Dark Web requires more proactive efforts compared to traditional security. It demands cyber security experts and technical resources combined with an innovative approach.
The Malaysian government has to introduce a dedicated cybercrime unit to tackle the Dark Web. For short-term measures, the relevant law enforcement agencies and regulators should form a task force with Cybersecurity Malaysia and acquire the capabilities pertaining to Deep Web analysis. This is to enable the task force to effectively conduct investigations on serious criminal activities operating in the Dark Web.
For long-term planning, the Government may consider forming a federal crime agency with a range of specialist capabilities to fight serious organised crime. The agency can respond to a wide range of threats including cybercrime, drug, human and weapons trafficking and economic crime. In 2013, the UK government formed the National Crime Agency (NCA) to fight serious and organised crime.
This law enforcement intelligence-led agency has launched a dedicated cybercrime unit to tackle the dark Web. Finally, Malaysia should also introduce a national plan to fight cybercrime. According to the 2014 Global Economic Crime Survey by PricewaterhouseCoopers (PWC), cybercrime will likely emerge as “the most popular” type of economic crime in Malaysia as more IT-related transactions are made in the future.
Prevention and mitigation are other vital aspects in fighting cybercriminals and terrorists especially in the Dark Web. My personal opinion Before I write my opinion I would like to say that Most Malaysians learnt about The Dark Web following the recent of a heinous crime committed by a British pedophile.
It emerged during the trial in which pictures and illicit videos were found posted on The Dark Web.my advice to every one is you must do security tips to help the Internet users minimize the risk of personal data: Update Web Browser, Change Passwords Regularly, Data Encryption.
Be Wary of Public Wi-Fi Filter what you share on Social Networking sites In my opinion, The Malaysia Police must cooperate with Cybersecurity Malaysia to track down organized criminal activities such as pedophiles in the country as the Director of the Institute of Crime and Criminology, University HELP, Datuk Akhbar Satar said above .
Source : http://www.thestar.com.my/opinion/letters/2016/06/24/tackling-dark-web-of-crime/
https://www.youtube.com
https://www. imdb.com/